
Incentive programs are powerful tools for businesses, but they’re also prime targets for fraudsters. At Reward the World, we’ve seen firsthand how abuse can erode trust and profitability.
This post explores effective loyalty fraud prevention strategies to protect your incentive program. We’ll cover key verification systems, clear terms and conditions, and ongoing vigilance to keep your rewards safe and your customers happy.
Common Incentive Program Abuses and Their Impact
Incentive program abuse poses a significant threat to businesses across industries. This chapter explores various tactics fraudsters use to exploit reward systems and the consequences of these actions.
Account Takeover Fraud
Account takeover fraud stands out as one of the most prevalent forms of abuse. Cybercriminals gain unauthorized access to legitimate user accounts through methods like phishing or data breaches. Once inside, they drain accumulated points or redeem rewards for high-value items.
Point Farming
Point farming involves the creation of multiple fake accounts or exploitation of system loopholes to accumulate points artificially. Fraudsters often use bots to automate this process, generating thousands of illegitimate points in a short time.
Reselling Rewards
Some individuals abuse incentive programs by redeeming points for gift cards or products, then reselling them for cash. While not always explicitly forbidden, this practice can significantly devalue rewards and impact program economics.
Impact on Businesses
The consequences of incentive program abuse extend far beyond immediate financial losses. Moreover, program abuse erodes trust and can damage brand reputation, potentially leading to customer churn.
Effects on Legitimate Customers
Honest participants also suffer from the actions of fraudsters. When criminals deplete reward inventories or cause businesses to tighten redemption policies, legitimate customers find their hard-earned points less valuable or harder to use.
Red Flags of Potential Abuse
Early identification of potential fraud plays a key role in minimizing its impact. Businesses should watch for these warning signs:
- Sudden spikes in account creations or point accumulation
- Multiple accounts linked to the same IP address or payment method
- Unusual patterns of high-value redemptions
- Accounts with minimal activity suddenly redeeming large amounts of points

Advanced monitoring systems (like those offered by leading platforms such as Reward the World) can help detect these anomalies. These tools flag suspicious activity in real-time, allowing businesses to take swift action against potential fraud.
The next chapter will explore effective strategies for implementing strong verification systems to prevent these types of abuse and protect the integrity of your incentive program.
How to Bulletproof Your Verification Systems
Strengthen Authentication
Multi-factor authentication (MFA) stands as a powerful tool in your fraud prevention arsenal. MFA requires users to provide two or more verification factors, which significantly reduces the risk of unauthorized access. A 2022 Microsoft study revealed that MFA blocks 99.9% of automated attacks on accounts.
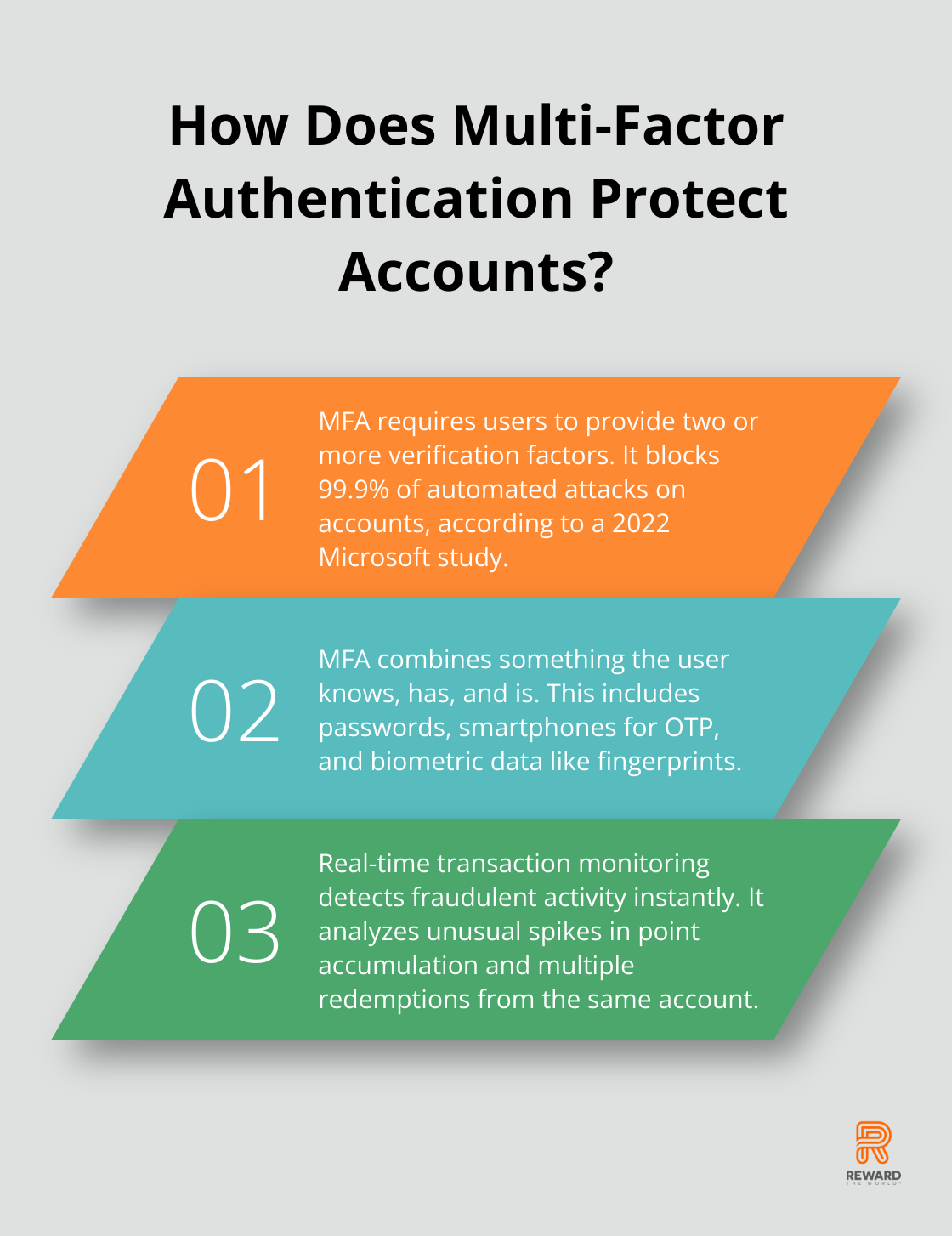
Implement a combination of:
- Something the user knows (password)
- Something the user has (smartphone for OTP)
- Something the user is (biometric data like fingerprints)
For high-value transactions or account changes, step up authentication by requiring additional verification steps.
Monitor Transactions in Real-Time
Real-time transaction monitoring allows you to detect and prevent fraudulent activity as it happens. Advanced machine learning algorithms analyze patterns and flag suspicious behavior instantly.
Key metrics to monitor include:
- Unusual spikes in point accumulation
- Multiple redemptions from the same account in a short time frame
- High-value redemptions from newly created accounts
Many incentive platforms offer built-in real-time monitoring capabilities (Reward the World being a top choice), allowing businesses to set custom alert thresholds and automate responses to potential fraud attempts.
Leverage Device and Location Intelligence
Tracking IP addresses and device information provides valuable context for user activity. Sudden changes in login location or device can indicate potential account takeover attempts.
Implement device fingerprinting technology to create unique identifiers for each user’s device. This makes it easier to spot when multiple accounts are accessed from the same device – a common tactic in point farming schemes.
Geolocation data can also help identify suspicious activity. For example, if a user typically accesses their account from New York but suddenly logs in from multiple international locations within a short timeframe, it warrants investigation.
Balance Security and User Experience
While robust verification systems are essential, it’s important to strike a balance between security and usability. Overly cumbersome verification processes can frustrate honest customers and impact program engagement. Try to implement security measures that provide strong protection without creating unnecessary friction for legitimate users.
Clear terms and conditions play a vital role in protecting your incentive program from abuse. The next chapter will explore how to craft effective program rules that deter fraud while setting clear expectations for participants.
Crafting Ironclad Terms and Conditions
Define Acceptable Use
Clear, comprehensive terms and conditions form your first line of defense against incentive program abuse. Well-defined rules protect your business and set expectations for participants, creating a fair and transparent environment for all.
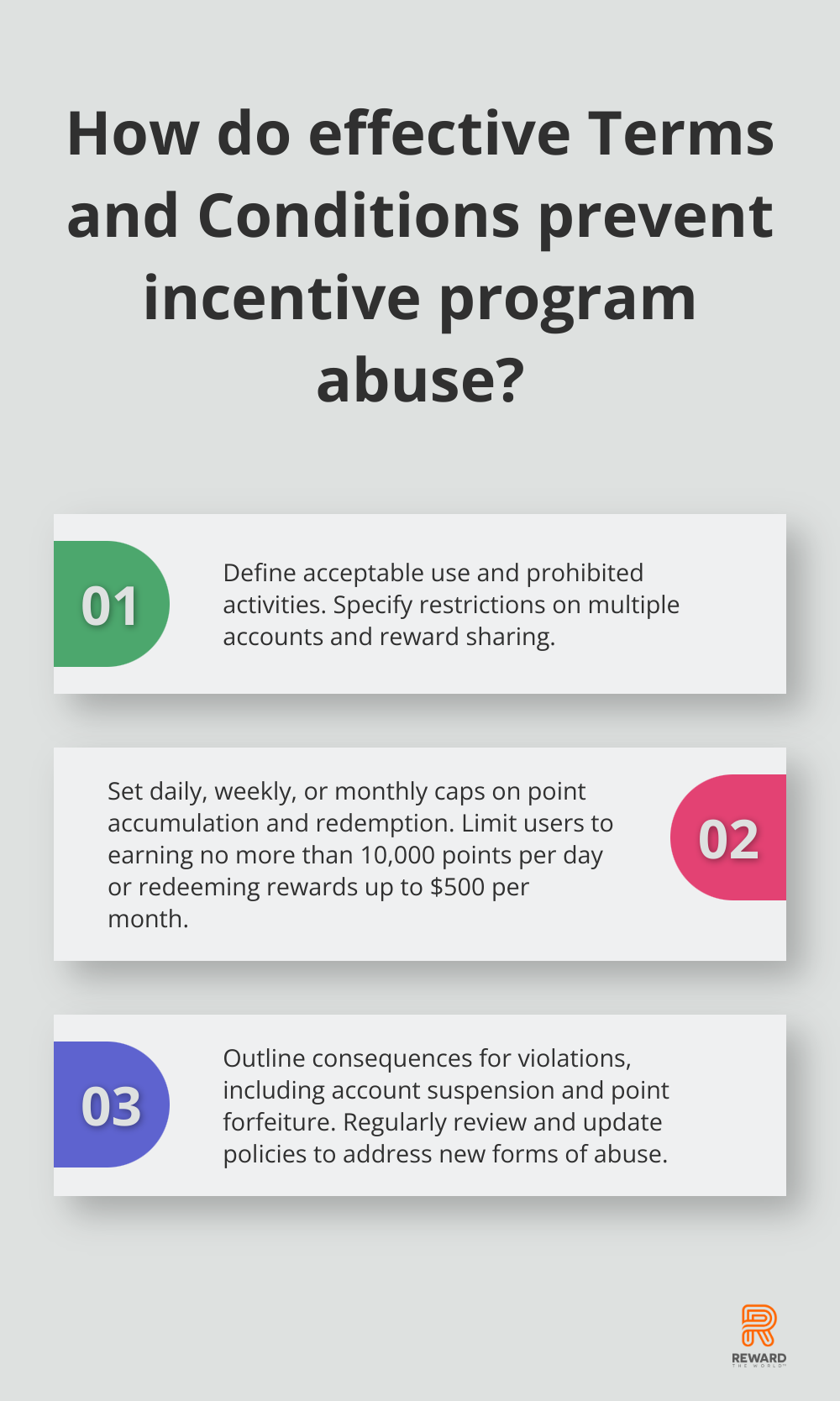
Start by outlining what constitutes acceptable program use. This includes how users can earn points, what activities are prohibited, and any limitations on participation. Specify if users can create multiple accounts or if there are restrictions on sharing rewards.
Set Accumulation and Redemption Limits
Restrictions on point accumulation and redemption can significantly reduce the risk of abuse. Set daily, weekly, or monthly caps on the number of points a user can earn or redeem. This strategy prevents point farming and unusual activity spikes that often signal fraudulent behavior.
You might limit users to earning no more than 10,000 points per day or redeeming rewards worth up to $500 per month. These limits should accommodate legitimate users but restrict potential abuse.
Outline Consequences for Violations
Communicate the consequences of violating your program’s terms and conditions. This may include account suspension, point forfeiture, or permanent program banning. Be specific about what actions will trigger these penalties.
Consult Legal Experts
When you craft your terms and conditions, consult with legal experts to ensure compliance with relevant laws and regulations. Review and update your policies regularly to address new forms of abuse as they emerge.
Balance Security and User Experience
The goal is to create a secure environment that protects your business while still providing value to honest participants (striking this balance is key to maintaining a successful and trustworthy incentive program).
Many leading incentive platforms offer tools to help businesses implement and enforce strong terms and conditions, ensuring both security and a positive user experience.
Final Thoughts
Protecting your incentive program from abuse requires a multi-faceted approach. Robust verification systems, clear terms and conditions, and constant vigilance reduce fraud risk while preserving a positive experience for legitimate users. Multi-factor authentication, real-time transaction monitoring, and device tracking create formidable barriers against common abuses like account takeovers and point farming.

The key lies in striking the right balance between security and user experience. Overly restrictive measures can frustrate honest customers and harm engagement. Regular review and adaptation of your security strategies are essential as fraudsters continually evolve their tactics.
Reward the World offers businesses a powerful suite of tools to protect their loyalty programs. With built-in security features, real-time monitoring capabilities, and support for clear terms and conditions, we help companies safeguard their incentives (while delivering a seamless experience to users worldwide). Effective loyalty fraud prevention is an ongoing process that requires vigilance, adaptability, and the right technological support.
